Researchers from 5 American schools have collectively developed this facet-channel assault
cell safety is kind of like a freeway: new potholes type day-after-day and its throughput capabilities are extremely counting on the drivers taking care to not set off a pile-up. whether or not these crashes are launched on by researchers sniffing out a mannequin new vulnerability, gamers down the safety chain not doing their half, or worse. a gaggle of researchers from simply a few of America’s most reputed educational institutions has now developed an assault named EarSpy, designed to grab what clients say by curiously artful means.
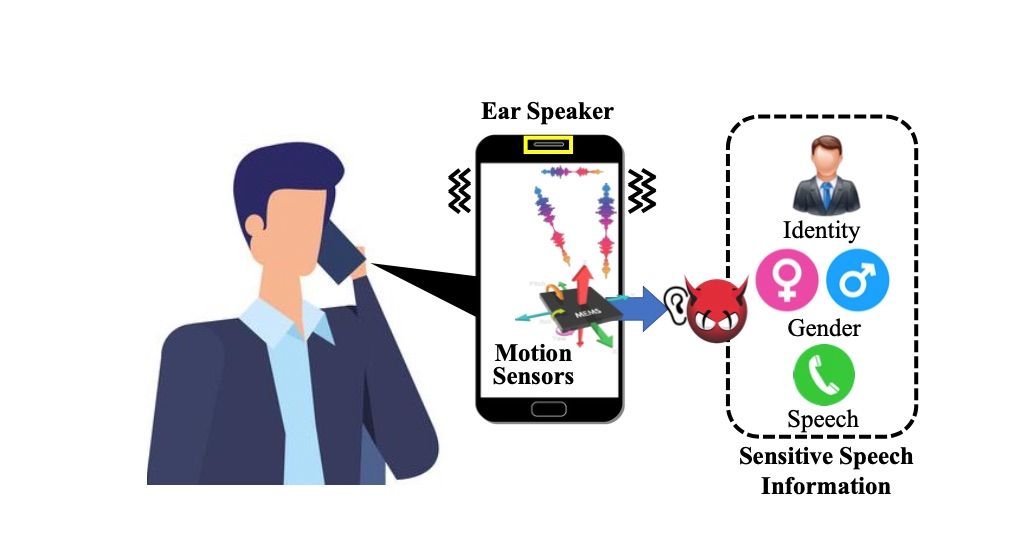
This effort is being carried out collectively by consultants from the college of Dayton, New Jersey Institute of know-how, Rutgers college, Texas A&M college, and Temple college. Researchers have tried to collect vibrations from a cellphone’s loudspeaker up to now, however this particular assault is efficient even when the person is holding the cellphone to their ear, SecurityWeek studies.
The evaluation group examined out EarSpy on the OnePlus 7T and the OnePlus 9 smartphones with astonishingly right outcomes using nothing however knowledge from the earpiece and the onboard accelerometer. in opposition to this, the knowledge was laborious to grab on older OnePlus fashions consequently of lack of stereo audio system, the researchers said of their paper. They examined the reverberations generated on the ear speaker with the assist of spectrograms and time-frequency area function extraction. the primary goal of the group was to decide the gender of the speaker and the contents of the speech itself — if not already recognized, attackers may be succesful to get hold of out the id of the speaker.
Newer Android variations have a extra strong safety gear, making it exceedingly tough for malware to get the requisite permissions. however EarSpy assaults can nonetheless bypass these constructed-in safeguards as uncooked knowledge from a cellphone’s movement sensors are simply accessible. although extra producers at the second are placing limits on buying knowledge from the gadget’s sensors, EarSpy researchers take into account it is nonetheless potential to infiltrate the gadget and hear in on a dialog.
As for the effectiveness of this assault, the researchers say EarSpy may appropriately inform the distinction between women and males in as a lot as ninety eight% of the circumstances. furthermore, it may detect the particular person’s id with a ridiculous ninety two% extreme accuracy price. nonetheless, this dips to fifty six% in relation to actually understanding what was spoken. Researchers say that is nonetheless 5x extra right than making a random guess.
In concept, EarSpy may be leveraged by malware that has infiltrated the gadget and relay the knowledge again to the supply of the assault. This report highlights the significance of extra hardware safeguards, particularly with parts like movement sensors that mustn’t be going to look like simple targets at first look.
To remedy this potential vulnerability in trendy-day smartphones, the researchers suggest smartphone makers to place the movement sensors away from any supply of vibrations whereas additionally reducing sound stress all by cellphone calls.




0 Comments