there are a lot of causes it is advisable to maintain people from viewing your information. presumably it accommodates delicate information, or it might presumably be dangerous if the incorrect particular person sees it. it does not matter what the purpose, on-line privateness will always stay a reputable concern. whereas many privateness-defending options are current in iPhones and lots of the extreme Android telephones, not all of these options work everytime you make the most of third-get together apps. finish-to-finish encryption, nonetheless, is a reasonably efficient privateness machine that is altering into more and more trendy in messaging apps.
however what precisely is finish-to-finish encryption? How can it preserve completely different people from seeing your information? briefly, it is a approach of scrambling information in your machine earlier than it is despatched. It does so in a approach that solely permits the meant recipient to decode the message. even when a messaging app shops your scrambled message on its servers or if an undesirable third get together intercepts the scrambled message, the encrypted information is ineffective by itself. the one one which can decode the scrambled message (theoretically, no decrease than) is the particular person you despatched your message to.
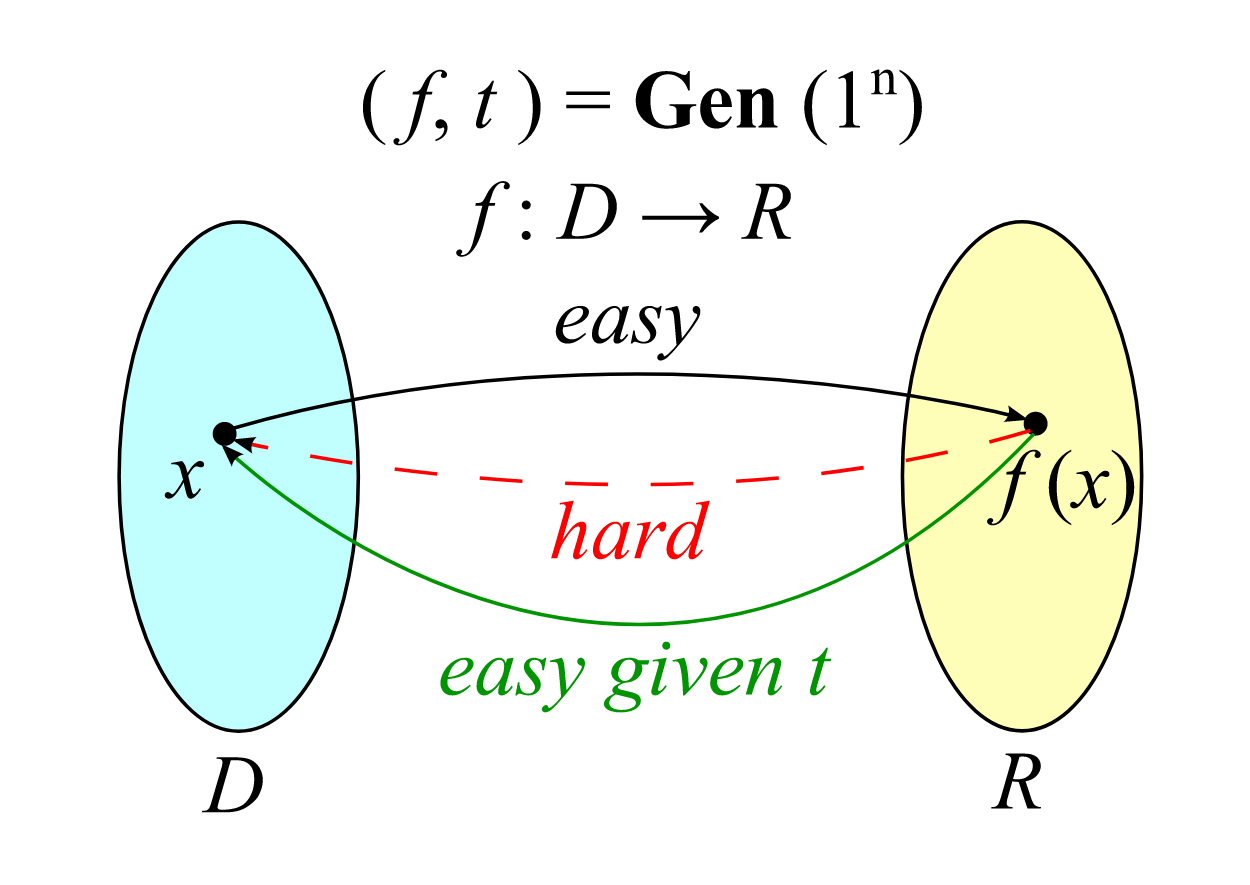
finish-to-finish encryption’s private and non-private keys
every that makes use of finish-to-finish encryption has two numbers acknowledged as “keys.” One secret’s the “public key,” which anyone can see. The second key, the “private key,” is stored secret from everyone, collectively with the app’s creators. the whole public secret’s used to encode a message, and this encoded message can solely be decoded using its corresponding private key.
supply: Wikimedia Commons / rahmatagungj
When any particular person sends you an encrypted message, their app makes use of your public key to encrypt the message. The encrypted message is distributed over the on-line. nonetheless, the whole public key can not be used to translate the message into its real type. to do this, you’d like your private key. that is attainable as a consequence of the whole public key and private key are linked in a approach that is almost unattainable to get your hands on out when trying on the whole public key alone.
the flowery math behind finish-to-finish encryption
know-how, as a consequence of it exists as we converse, can not decide somebody’s private key. The trick to the tactic is that this: figuring out somebody’s private secret’s borderline unattainable using current know-how. producing the two keys entails using a one-approach function. This one-approach function is a calculation that is straightforward for a laptop computer to carry out however takes an limitless quantity of computing power to reverse. Reversing the function turns into almost unattainable when these features are carried out on large enough numbers, resembling a sixty 4-digit private key.
supply: Wikimedia Commons / IkamusumeFan
One straightforward form of 1-approach function is to take a quantity, sq. that quantity, divide it by the product of two prime numbers, and take the relaxation. everytime you already know the two prime numbers, it is straightforward to reverse the function and decide the distinctive quantity. nonetheless, it requires brute drive to get your hands on out the distinctive quantity with out the prime numbers. If the two prime numbers are large enough, no laptop computer on this planet has the computational power needed to brute drive the reply.
discovering one other particular person’s private key makes it straightforward to decrypt a message. Many apps usually swap prospects’ private and public keys to mitigate this challenge. Discovering a consumer’s private key for one among these apps solely decodes a quantity of messages. the relaxation stay encrypted and unintelligible.
Which communication apps use finish-to-finish encryption?
it is one factor to know what finish-to-finish encryption is. however that information is hardly useful everytime you do not know which apps use it. the following apps have finish-to-finish encryption both as an selection or enabled by default.
signal
signal is a singular messaging app. Not as a outcomes of its options however as a outcomes of its underlying philosophy. The free app, which has finish-to-finish encryption for all its messages, was made by the nonprofit signal basis. This basis has the said purpose of creating open supply privateness know-how for communications. as a outcomes of this, signal is an open supply app, as is its underlying encryption protocol acknowledged as the signal Protocol. This protocol has been utilized by a quantity of completely different apps, collectively with Meta’s WhatsApp, Google’s now-defunct Allo, and Microsoft’s Skype.
Threema
Threema is one other messaging app with finish-to-finish encryption enabled for all its messages. nonetheless, the philosophy driving Threema’s creators, the swill agency Threema GmbH, might not be extra completely different from signal’s. Threema is a proprietary app, so the exact approach it features is simply not open to the whole public. it is additionally a paid app, which means you should fork out $5.00 to place it to use. Threema additionally gives a self-hosted mannequin of its computer software that firms can set up on their very personal servers in the event that they want further safety.
WhatsApp is the world’s hottest messaging and video chat app, with about two billion month-to-month lively prospects throughout the globe. whereas it is decently trendy in america, the residents of some nations use it as their major messaging app almost solely. for event, ninety six% of South Africans use WhatsApp, as do ninety three% of Argentinians and ninety one% of Brazilians.
WhatsApp makes use of the identical finish-to-finish encryption protocol as signal. The app mechanically permits this encryption for its messaging and enterprise messaging features, and also you’d possibly activate finish-to-finish encryption to your message backups.
Telegram
not like signal, Threema, and WhatsApp, Telegram does not mechanically allow finish-to-finish encryption for its prospects. nonetheless, secret chats use finish-to-finish encryption. any such chat can solely be used when the recipient is on-line. Telegram has completely different privateness-acutely conscious options, resembling self-destruct timers that erase secret messages and a setting that mechanically deletes your account after a set interval of inactivity.
fb Messenger
Since Meta owns fb and WhatsApp, it ought to not be a shock that fb Messenger has finish-to-finish encryption. nonetheless, not like WhatsApp, fb’s finish-to-finish encryption performance does not apply to all messages. To allow finish-to-finish encryption in fb Messenger, you should click on the “i” button inside the elevated-proper nook of an current dialog, then choose the selection to activate secret conversations. Secret conversations even have the selection to delete messages mechanically after a set timeframe.
Wire
whereas so a lot of the apps above solely supply finish-to-finish encryption for messages, Wire has a wider fluctuate of communications that it’d presumably encrypt. collectively with messages, Wire can apply finish-to-finish encryption to its file-sharing, voice calls, video calls, and convention calls with as a lot as 25 completely different individuals with out delay. Wire additionally has staff collaboration capabilities, that are additionally finish-to-finish encrypted.
Google Messages
Google’s default texting app for Android gadgets is a current addition to the guidelines of apps with finish-to-finish encryption. whereas the extreme-to-finish encryption performance is at the second in beta, Android prospects can use the beta mannequin by choosing the flip proper into a tester selection from the play retailer. If each events to a dialog have chat options enabled, all messages and eligible attachments are mechanically finish-to-finish encrypted.
finish-to-finish encryption is simply not great
everytime you hear with reference to the know-how behind finish-to-finish encryption, it is in all probability tempting to imagine that it is unbeatable. nonetheless, there are extra issues to maintain in thoughts moreover the cryptography. it is in all probability simply bypassed, for event, by somebody who has entry to your cellphone and is aware of your password. people who fall prey to phishing assaults are additionally susceptible, regardless of what quantity of of their apps have finish-to-finish encryption.
finish-to-finish encryption additionally does not shield you from dishonest builders. an group can declare that it gives finish-to-finish encryption, however it absolutely might have carried out it improperly or added a backdoor that permits outsiders to study your messages. finally, you must have the power to notion the app developer for finish-to-finish encryption to be in any respect useful.
extra methods to shield your self
Encryption is one among many methods to maintain your privateness intact on-line. completely different useful steps you will have the power to take contain enabling two-challenge authentication, opting out of information assortment when attainable, and opting out of focused promoting. Our article with reference to the right approach to enhance privateness in your Android cellphone is an environment nice place to start on the matter of studying what you will have the power to do to maintain your information safe, or no decrease than as safe as attainable, on this modern world.


.png)

0 Comments